Synthetic approach of symbolic creatures
© This paper is not for reproduction without permission of the author(s).
1 Introduction
We propose, based on the Peircean semiotics and inspired by an ethological case, a methodology to simulate the emergence of symbolic predator-warning communication among artificial creatures in a virtual world of predatory events. In order to build a digital ecosystem, and infer the minimum organizational constraints for the design of our creatures, we examined the well-studied case of semiosis in East African vervet monkeys (Cercopithecus aethiops).
The article is divided into:
(i) a brief summary of Peircean semiotics,
(ii) a semiotic analysis of the vervet monkey alarm-call system;
(iii) a description of a virtual environment inhabited by an interactive community of artificial creatures.
2 The Peircean theoretical semiotics
The Peircean list of categories (Firstness, Secondness, Thirdness) constitutes an exhaustive system of hierarchically organized classes of relations (monadic, dyadic, triadic) (Houser 1997: 14). In this context, and relatively to the ‘most fundamental division of signs’ (CP 2.275), these classes correspond to icons, indexes and symbols that correspond to relations of similarity, contiguity, and law between S-O (sign-object) of the triad S-O-I (sign-object-interpretant).
Icons are signs which stand for their objects through similarity or resemblance (CP 2.276) irrespective of any spatio-temporal physical correlation that S has with existent O – ‘An Icon is a sign which refers to the Object that it denotes merely by virtue of characters of its own, and which it possesses, just the same, whether any such Object actually exists or not’ (CP 2.247; see 8.335, 5.73). In contrast, if S is a sign of O by reason of a dyadic relation with O, then it is said to be an index of O – ‘An Index is a sign which refers to the Object that it denotes by virtue of being really affected by that Object. […] [Insofar] as the Index is affected by the Object, it necessarily has some Quality in common with the Object, and it is in respect to these that it refers to the Object. It does, therefore, involve a sort of Icon’ (CP 2.248; see 2.304). Finally, if S is in a triadic relation with O, it is a symbol of O, and the determinative relation of S by O, a relation of law – ‘A Symbol is a law, or regularity of the indefinite future. […] But a law necessarily governs, or ‘is embodied in’ individuals, and prescribes some of their qualities. Consequently, a constituent of a Symbol may be an Index, and a constituent may be an Icon’ (CP 2.293; see 2.299, 2.304, 2.249).
3 A semiotic analysis of vervet monkey alarm calls
In order to get insight into the design of the creatures, we started by performing a semiotic analysis of vervet monkeys’ intra-specific communication (Queiroz & Ribeiro 2002). Field studies (Strushaker 1967; Seyfarth et al. 1980) have revealed three main kinds of alarm calls used to warn about the presence of imminent predation: (a) terrestrial stalking predators such as leopards, (b) aerial raptors such as eagles, and (c) ground predators such as snakes. When a “leopard” call is uttered, vervets escape to the top of nearby trees; “eagle” calls cause vervets to hide under trees, and “snake”calls elicit rearing on the hindpaws and careful scrutiny of the surrounding terrain.
Consider two stimuli available to a vervet monkey: the view of a predator and an alarm-call played through a loudspeaker. The sensorial responses that code for the physical features of the visual image of the predator and the corresponding alarm-call are iconic representations of their objects (Zaretsky & Konishi 1976; Tootell et al., 1988; Ribeiro et al. 1998). In principle, the mere visualization of a predator should be enough to generate an escape response. In contrast, the physical properties of the acoustic alarm-call (amplitude and frequency) do not stand for the leopard in any intrinsic way. In the absence of a previously established relationship between that call and the predator, the former will simply arouse the receiver’s attention to any concomitant event of interest, generating a sensory scan response directed to the loudspeaker and its surroundings (Seyfarth et al. 1980). At least two things may happen then: (i) if nothing of interest is found, the receiver should stay put; (ii) if a predator is spotted stalking nearby, or if other vervet monkeys are observed fleeing to a neighboring refuge, the receiver might be prompted to flee. In these cases the alarm-call could have been interpreted as an index either of the predator or of collective vervet monkey escape, with identical behavioral outcomes. But during a experiment conducted by Seyfarth et al. (1980), even though there were no predators in the visual scene, adult (but not infant) vervet monkeys proceeded by fleeing to nearby refuges according to the specific type of call played (“leopard” calls evoked tree-climbing, “eagle” calls elicited bush hiding etc).
If the alarm-call operates in a sign-specific way in the absence of an external referent, then it is a symbol of a specific predator class. This symbolic relationship implies the association of at least two representations of a lower order (i.e., indexes or icons) in a higher-order representation domain, which should be able to command escape responses. As discussed above, sensory stimuli present in the world are iconically represented in the monkey’s perception system. The representation of an alarm-call alone cannot evoke any predator-specific meaning, and therefore will fail to cause an escape response. Presented together, the two stimuli can be interpreted as bearing an indexical relationship, i.e., the alarm is an index of the predator’s presence, generating an escape response. The existence of a higher-order domain of representation, which associates responses of both sensory modalities, enables the monkey to interpret an alarm-call presented alone as a symbol of its referent, i.e., the predators view, followed by an escape response.
The framework applied here to the case of vervet monkey alarm calls guided our experiments of simulating semiosis among artificial creatures in a virtual world.
4 Designing a virtual scenario
This is a project on synthetic ethology where we simulate an ecosystem that allows cooperative interaction between agents, including intra-specific communication, a property that provides selective advantage in an environment of predatory events. The virtual world will work as a laboratory to simulate the emergence of anti-predatory alarm call vocalization among creatures under the risk of predation.
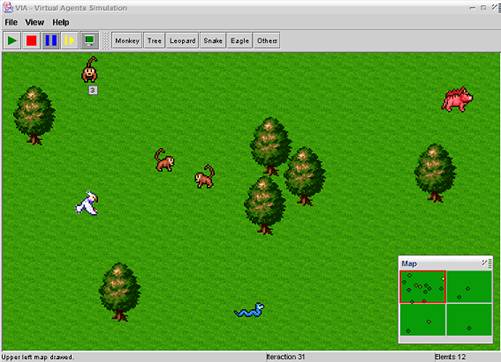
Figure 1: The Virtual Agents Simulation, used to simulate the creatures’ interactions.
4.1 Virtual Environment and Creatures
Our virtual world is composed of creatures divided into preys and predators, and also of objects such as trees (climbable objects) and bushes (used to hide). There is only one type of prey with two distinct roles – teacher and learner – but there are three types of predators: terrestrial predator, aerial predator and ground predator. The preys can be teachers, which already know the alarm calls for each predator, or learners, which don’t know the alarm calls and try to find what they are related to.
The creatures are autonomous, graphically embodied agents in an interactive, 2D virtual environment. They have sensors and motor abilities that make possible their interactions with the virtual environment. The sensorial apparatus of preys includes hearing and seeing, but predators can only see. The creatures also have interactive abilities defined by a set of possible individual actions, such as: adjustment of sensors, movement, attack, climb on tree, hide under bush and vocalize alarms. The last three actions are specific to preys. On the other hand, attacks are specific of predators.
Both the prey and predator creatures are controlled by action selection mechanisms (Franklin 1997; Brooks 1986; Tyrrell 1993), which allows them to choose from different conflicting actions given the environment’s and the creature’s internal states. Our action selection mechanism used by the creatures relies in the behavior-based approach (Brooks 1986), using drives, motivations and behaviors. Each behavior is an independent module that competes to be the active one and control the creature. The behaviors provide their motivation values defining their intent to control the creature, given the sensorial data and the creature’s internal drives. The drives define ‘instincts’ or needs such as fear or hunger, updated at each instant based on external stimuli or time passing. This mechanism is not learned but rather designed, being simple to implement and yet having complex results, enabling the creatures to act in different ways.
4.2 Predators’ control architecture
Predators have a simple control architecture: they have only three basic behaviors - wandering, prey chasing and resting - and two drives - hunger and tiredness. The hunger drive is increased by time passing and set to a low value when a prey is attacked. The tiredness drive is increased when the predator moves too fast and decreased when it stops moving. The prey chasing behavior makes the creature move in the prey’s direction until it gets close enough to be attacked. Its motivation is proportional to hunger drive, when it is high and a prey is seen; or null, otherwise. The resting behavior makes the predator move at null speed, and provides a motivation value relative to tiredness drive. The wandering behavior has a constant motivation value and makes the creatures move in a random direction with random speed.
4.3 Preys’ cognitive architecture
The prey has a larger set of behaviors, including those involved in communication support. Communication related behaviors are vocalizing, scanning, associative learning, and following. Other them these ones, the preys also have basic behaviors, such as wandering, fleeing and resting. Related to all these behaviors, the preys have different drives: boredom, tiredness, fear, solitude and curiosity.
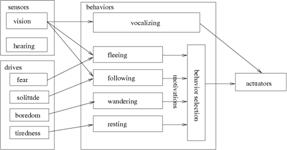
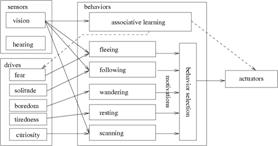
(a) (b)
Figure 2: The prey’s cognitive architecture: (a) the teacher prey has a vocalizing behavior which makes them vocalize a alarm in the presence of a predator, and (b) the learner prey has a associative learning behavior, enabling referential learning of alarms and scanning behavior for searching for a possible referent.
The boredom drive indicates how active or not the creature is, increasing when it is not moving and decreasing, otherwise. The tiredness drive is updated when the prey moves too fast, or when it is not moving, in the same way as the predator. The fear drive is related to the presence of a predator, jumping to a high value as soon as the prey sees the predator, and decreasing when it is not in sight. The solitude drive expresses a desire to be next to other similar creatures, decreasing when another prey is seen and increasing when not seen. And the curiosity drive describes the state of the prey after it hears an alarm. This drive is only pertinent to the learner and jumps to a high value as soon as it hears an alarm, and is decreased after that.
The learner and the teacher don’t have exactly the same behavior as they have different roles. The teacher has a vocalizing behavior and the learner has an associative learning behavior and a scanning behavior. The vocalizing behavior makes the teacher prey emit an alarm when it sees a predator, having three types of alarms, for each of three types of predator. The learner’s associative learning makes associations between auditory and visual sensorial stimulus using a self-organizing associative memory described in the next section. The scanning behavior makes the prey search for the vocalizer and try to follow its visual attention in order to find a possible referent, having its motivation set to the value of curiosity drive, if an alarm is heard. The following behavior causes the preys to follow a companion by trying to stay within a maximum and minimum distance from it, proving motivation equal to the solitude drive when another prey is seen. The fleeing behavior makes the prey run away from the predator, until its fear goes down, with motivation proportional to the fear drive. The wandering behavior will keep the prey moving eventually turning direction left/right sometimes, setting motivation equal to boredom drive, if the prey is not moving. The resting behavior stops the prey’s movement when the tiredness drive is getting too high.
4.4 Associative learning
We propose that associative learning is the mechanism used by the vervet to learn the relationships between the vocalizations produced by other vervets and the presence of a threat or predator including a possible escape response. Associative learning allows the prey to generalize temporal and spatial relationships between external stimuli from particular instances. If a teacher prey emits an alarm call, the learner prey will respond by scanning its surroundings, and when the learner detects a relevant visual stimulus, like the image of a predator, then the associative strength between the call and this visual stimulus will be incremented. This clearly increases the probability of an appropriate behavioral response (e.g. escape) whenever in the future the learner detects an alarm-call.
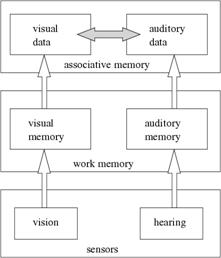
Figure 3: Associative learning, from sensors to associative memory.
Sensorial data from vision and hearing are received by the respective work memories. The work memory is a temporary repository of sensorial stimuli: when a stimulus is received from the sensor it is put in the work memory with maximum strength. During the subsequent instants, this strength is reduced until it gets to null value and is taken out of the work memory. This makes possible that stimuli received in different instants coexist for some time, bringing in temporal relations.
The items in the work memories are used by the associative memory to produce associations between the items from visual work memory and hearing work memory. When sensorial data is received in the work memories, the associative memory creates, or reinforces, the association between the visual item and the hearing item, and inhibits changes in this association. Inhibition avoids multiple adjustments in the same association caused by persisting items in the work memory. When an item is dropped from the work memory, its associations not inhibited, i.e., not already reinforced, are weakened, and the inhibited associations have their inhibition partially removed. When the two items of an inhibited association are removed, the association ends its inhibition, being subject again to changes in its strength. These positive (reinforcement) and negative (weakening) adjustment cycles allows the memory to self-organize ending up with the correct referents to the alarms. The reinforcement and weakening adjustments for non-inhibited associations, with strengths limited to the interval [0.0; 1.0], are relative to the current strength and also to the strongest association with the alarm: when current strength is high reinforcements are high and weakening lower, and vice-versa, but the strongest association can reduce reinforcements and increase weakening, simulating lateral inhibition.
As shown in figure 2, the result of associating external visual and auditory inputs can have an effect in terms of behavioral output. Moreover, this structure can be made more complex by allowing associative learning to influence the output of the drive functions. Thus the prey creature reproduces this procedure, and so the fear drive in the learner prey creature is altered, being proportional to the association strength when an alarm related to a predator is heard. This allows associative learning to elicit a fleeing response. If a false alarm was played to the prey creatures, they would exhibit the same response as the vervet monkeys, i.e., show an external evidence that the creature is using a symbol for its selective advantage avoiding the predator.
5 Conclusion
Here we combined theoretical constraints derived from Peirce’s theory of sign with the description of a paradigmatic case of animal communication to investigate the mechanisms underlying minimal conditions for symbolic emergence and simulate this process. We suggested that symbols correspond to very simple and basic neurobiological phenomena widely present in the animal kingdom.
Empirical research on the vervet monkey alarm-call system revealed in particular that infantile and young adult vervets do not have the competence of either interpreting or emitting these calls efficiently (Cheney & Seyfarth 1990). It indicates thus that this system involves learning. Thus the ontogenetic acquisition of symbols should begin with the learning of indexical relationships between stimuli, reproducing their external spatio-temporal regularities as detected by the learner. Our simulations indicate that optimal learning performance will eventually result in a law-like relationship that can be generalized to other contexts, in particular to the case where a sign denotes a class of referents. In Peircean semiotics, these processes are well described in terms of icons, indexes and symbols. These three kinds of semiosis are hierarchically connected as icons are necessary to indexes and indexes are necessary to symbols.
Our approach brings a fresh contribution to linguistics, semiotics, ethology and experimental psychology. Taken together, the different aspects of the work presented here demonstrate that the predator-warning communication system possessed by vervet monkeys satisfies the criteria of symbol as established by Peircean semiotics.
Acknowledgments
We thank Alexander Mehler for insightful criticism of this work. We also thank David Izuka and Phillip Rodolfi for technical assistance. J.Q. is funded by a grant from FAPESP; A.L. is funded by a grant from CAPES; S.R. is funded by a Pew Latin-American Fellowship.
References
Brooks, R. A. 1986. A robust layered control system for a mobile robot. IEEE Journal of Robotics and Automation, RA-2, 14-23.
Cheney, D.L., & Seyfarth, R. 1990. How Monkeys See the World. Chicago: University of Chicago Press.
Franklin, S. 1997. Autonomous agents as embodied AI. Cybernetics and Systems, 28(6), 499-520.
Houser, N. 1997. Introduction: Peirce as a logician, in N. Houser, D. Roberts & J. Evra, eds., Studies in the logic of Charles Sanders Peirce, pp. 1-22. Indiana: Indiana University Press.
Kandel, E. R., Schwartz, J. H., & Jessell, T. M. 1999. Principles of Neural Science. New York:McGraw-Hill/Appleton & Lange.
Peirce, C.S. 1931-1935. The Collected Papers of Charles Sanders Peirce. Vols. I-VI. C. Hartshorne & P. Weiss, eds. Cambridge, Mass.: Harvard University Press.
Peirce, C.S. 1958. The Collected Papers of Charles Sanders Peirce. Vols. VII-VIII. A.W. Burks, ed. Cambridge, Mass.: Harvard University Press.
Queiroz, J. & Ribeiro, S. 2002. The biological substrate of icons, indexes and symbols in animal communication: a neurosemiotic analysis of Vervet monkey alarm-calls, in M. Shapiro, ed., The Peirce Seminar Papers 5, pp.69-78. New York: Berghahn Books.
Ribeiro, S., Cecchi, G.A., Magnasco, M.O., & Mello, C.V. 1998. Toward a song code: evidence for a syllabic representation in the canary brain. Neuron 21(2), 359-371.
Seyfarth, R., Cheney, D.L., & Marler, P. 1980. Monkey responses to three different alarm calls: evidence of predator classification and semantic communication. Science 210, 801-803.
Strushaker, T.T. 1967. Auditory communication among vervet monkeys (Cercopithecus aethiops) in S.A. Altmann, ed., Social Communication among Primates, pp.281-324. Chicago: University of Chicago Press.
Tootell, R.B., Switkes, E., Silverman M.S., & Hamilton, S.L. 1988. Functional anatomy of macaque striate cortex. II: Retinotopic organization. J Neurosci 8(5), 1531-68.
Tyrrell, T. 1993 Computational mechanisms for action selection. PhD Thesis, University of Edinburgh, Scotland.
Zaretsky, M.D., Konishi, M. 1976. Tonotopic organization in the avian telencephalon. Brain Res, 111, 167-171.